MoLuW (Metatwin on Linux using Wine)
During my internship at NVISO, I got the chance to work on a R&D project involving payload crafting. You can read more about my experience here. On top, there was the opportunity of implementing the Metatwin script in to the project. This is my blog post detailing the result and more!

Metatwin is a wel known script used in the security world, used for copying resources and signature from legitimate binaries to binaries containing payloads.
Requirements
The solution we are looking for must be able to run on a headless (no GUI) Linux distribution and preferably deployable in a docker container. This had to integrate with the original project.
What does Metatwin do?
The Metatwin script is build in Powershell. It uses 2 binaries, ResourceHacker.exe & Sigthief.exe. The ResourceHacker binary is used for first extracting the resource from a legitimate and overwriting existing resources on the target binary. The other binary SigThief; used for copying the signature from a legitimate binary to a target binary.
Identifying a solution
SigThief
We first have to find two solutions to replace the functionality of both binaries. We immediately have some help, with the fact that, when looking at the original SigThief repo, it contains a python script which has the same functionality as the binary.
ResourceHacker
For the second binary, ResourceHacker, we don't have that much luck. During the short research no Linux compatible versions were found.
Another option was copying the functionality of the ResourceHacker binary; by either using an alternative, or remaking it in another language. While I personally would have love to do that, it would have taken way too much time.
Last option was running the binary on Linux using some kind of package. Luckily there is something like that called Wine. This option had been floated around for some time during initial and prior discussion of the original project, but had not been explored further.
Working it out (practical)
With the course of the possible solution identified, the next step was testing it out. , As mentioned, the SigThief provided a python script, which was tested and performed exactly as the binary did. So, this part of the problem was solved.
For the usage of the wine package, some testing had to be performed. This was initially done on a GUI Kali Linux environment which would allow for seeing any windows visually as Wine would require a working display. Later on, this later resulted in some issues.
The command for running any Linux binary and specifically the ResourceHacker binary is as follows:
wine ResourceHacker.exe
Once the command is executed, you should see the window become visual as it does in Windows. Tt will take a little bit longer though on a Linux environment.
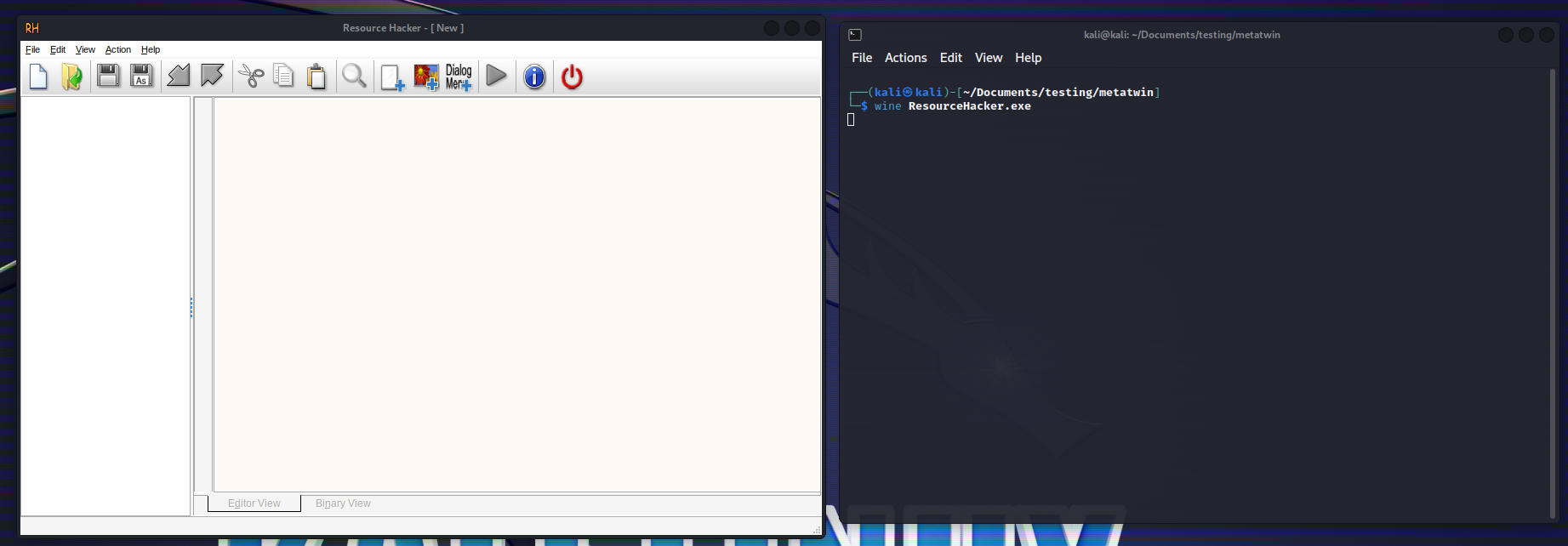
Now, the binary is running good, but does it function as expected? You can see a side by side, the binary running on the Kali Linux environment and on windows. The examined binary is the ADExplorer.exe which can be freely downloaded from the Microsoft website.
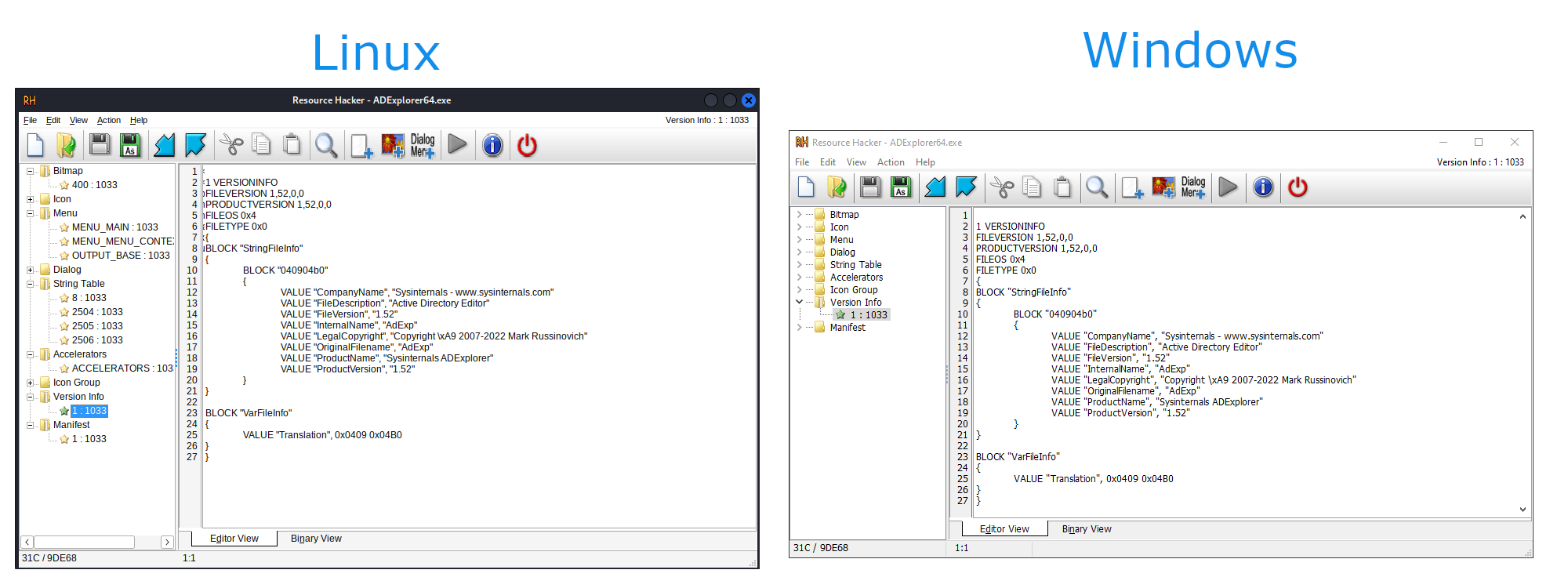
With the application running & working the next step is running the ResourceHacker binary with arguments, exactly as the original Metatwin script does.
Initially, I had some issues with passing arguments not working properly. Because of specifying wrongly formatted arguments, with everything fixed, the command for extracting resources looked something like this:
wine ResourceHacker.exe -open ./SourceBinary.exe -action extract -mask ,,, save ./resource.res -log ./log.log
It's important that the wine binary is used as that, waits for the binary that is executed to finish before exiting. The command for writing the resources to the target binary looks something like this:
wine ResourceHacker.exe -open ./TargetBinary.exe -save ./binary.exe_written -resource ./resource.res -action addoverwrite
It writes the resource from the extracted binary to a new binary. With both actions working properly, the next step was getting it to work in a docker container.
Docker
For the docker container, a base imaging node:bullseye was used as this was one of the requirements for the original project.
Before being able to run the binary in a headless Linux distribution, we require one extra package: xvfb. This package allows wine to run headless by running a virtual display using xvfb-run so wine can redirect its output and allow the underlying application to run.
Updating both commands with the new package in mind, we get the following:
Extracting resources:
xvfb-run wine ResourceHacker.exe -open ./SourceBinary.exe -action extract -mask ,,, save ./resource.res -log ./log.log
Writing resources:
xvfb-run wine ResourceHacker.exe -open ./TargetBinary.exe -save ./binary.exe_written -resource ./resource.res -action addoverwrite
With the commands updated, we can incorporate them in to a script that mimics the original Metatwin script functionality and run it in a docker file.
MoLuW (Metatwin on Linux using Wine)
All the files can be found in the following repo.
For the project, the logic for copying/writing the resources and signatures have been implemented in another language, but during testing, a python script was created to illustrate the concept.
Current implementation of the script can extract and overwrite available resources from a source binary to a target binary. The copying of the signature has also been implemented.
The original Metatwin script outputs the information from the digital signature after copying, that is present in the target binary if copying of the signature is required. The script currently does not have this feature, as this was not one of the requirements for the original project. However it is something that could be added in the future.
The current script has the options as showcased in the image available. You specify the source binary, target binary and if you would like to sign the executable.
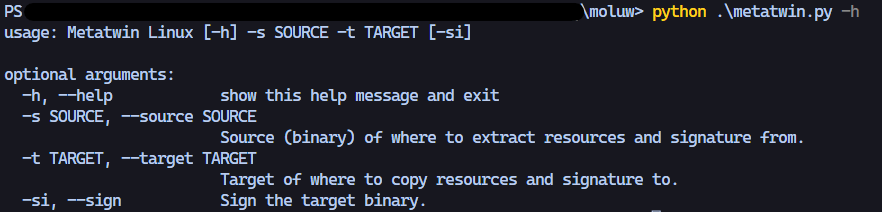
The complete command for running the script looks something like this:
python3 metatwin.py -s source-bin.exe -t target-bin.exe -si
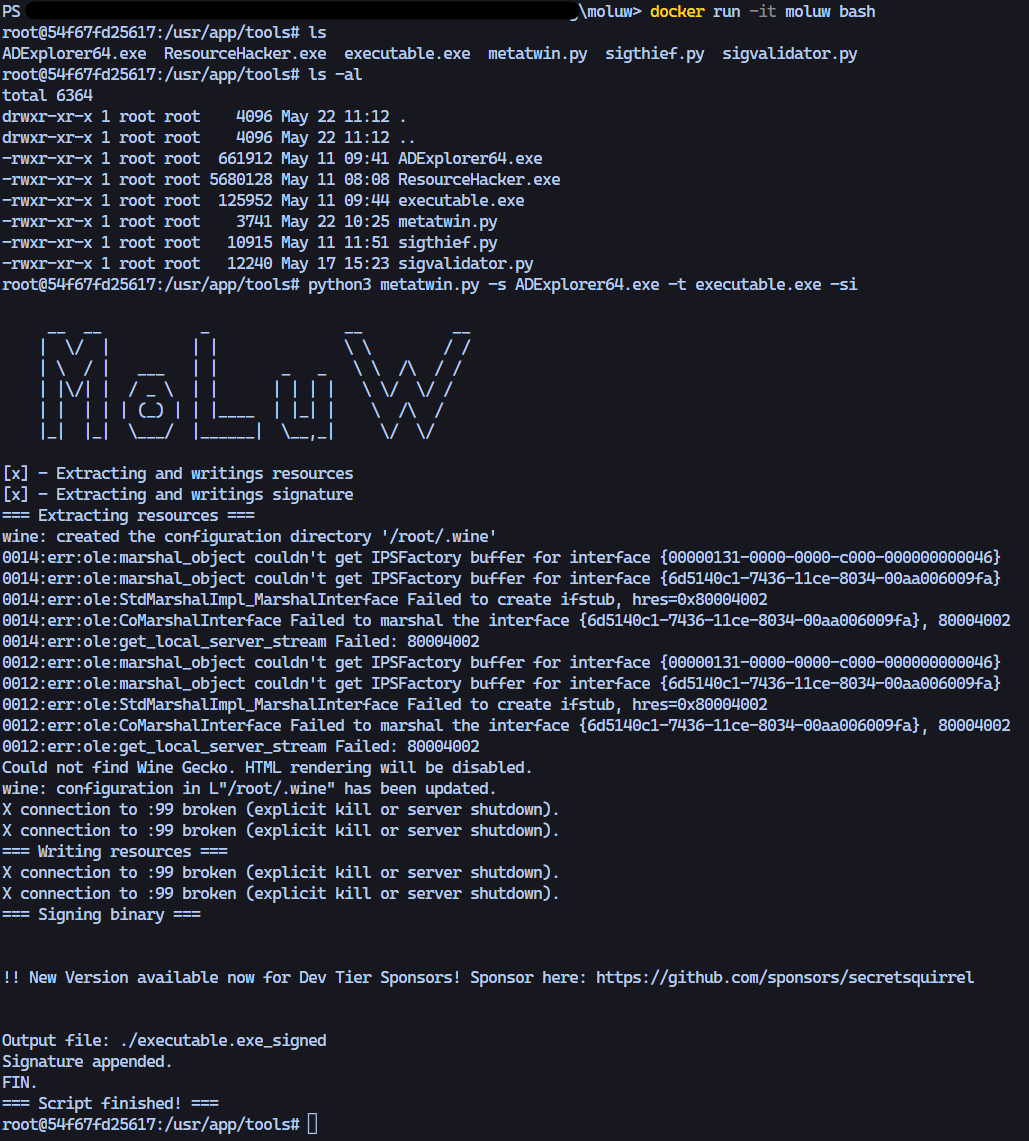
This results in the following output in the directory, the binary which we are the most interested in is the executable.exe_signed.
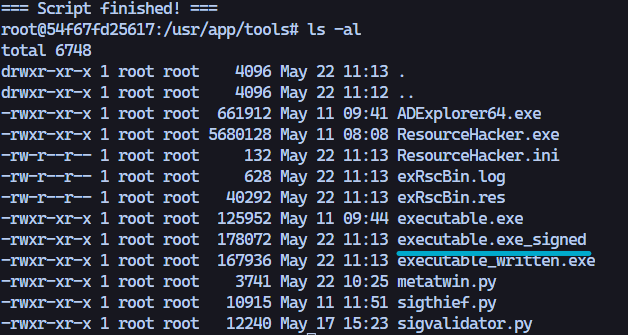
We can copy this binary to our host system using the docker cp command. Then, we can compare the before and after results.
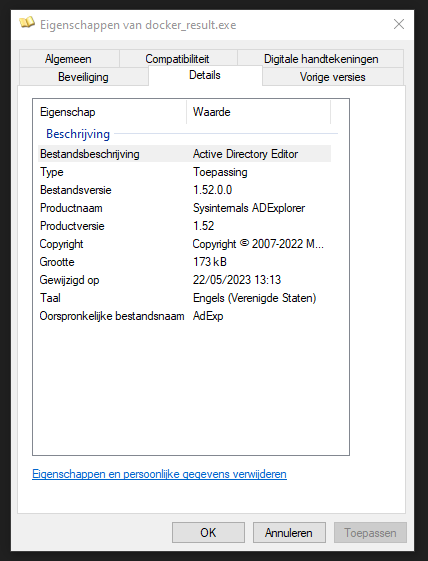
On the below image, you can see the details regarding the updated binary with the details matching the original ADExplorer64.exe binary.
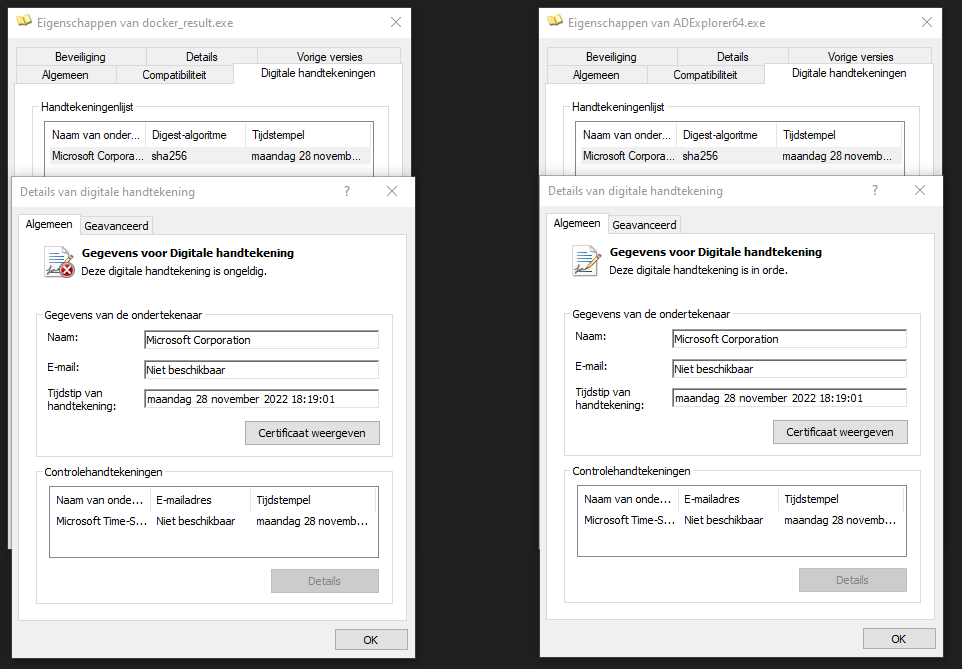
The result of copying the signature can also be seen in the below image. On the left, you have the signature attached to the updated binary and on the right, the original binary with its digital signature.
With both the resources and signatures copied from the original source binary to the target binary, the script has successfully completed its task.
Conclusion
With the MoLuW script add hand, its allows Red Teamers, to not require a Windows virtual machine for copying the resources and binaries to a payload binary. Greatly simplifying the process of readying a binary for further action.
The feature parity for the current version of the script is not complete, but the important parts are present.
With this conclusion, the blog post comes to an end. If you would like to read my complete journey of my international internship you can find the relevant blog post here.
This was an unpaid internship, but I was reimbursed for the cost of the apartment.